This is Part 2 of a pre-print draft of Chapter 6 from Smart Things: Ubiquitous Computing User Experience Design, my upcoming book. (Part 1) The final book will be different and this is no substitute for it, but it's a taste of what the book is about.
Earlier chapters in this series: Chapter 3, Chapter 1Citations to references can be found here.
Chapter 6: Information shadows
Part 2: Information shadows
Then Wendy saw the shadow on the floor, looking so draggled, and she was frightfully sorry for Peter. "How awful!" she said, but she could not help smiling when she saw that he had been trying to stick it on with soap. How exactly like a boy! Fortunately she knew at once what to do. "It must be sewn on," she said, just a little patronizingly.- Peter and Wendy by J. M. Barrie (1911)
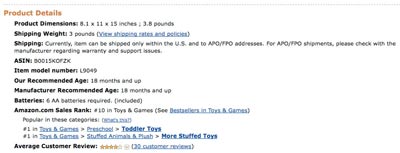
Figure 6-2. Amazon listing for Tickle Me Elmo, showing manufacturer metadata
An Amazon product listing (Figure 6-2) shows a lot of information, but there's much more information about the product than just the official specs. An enormous quantity of user-generated content exists on the Internet tied to nearly every product. Virtually everything made or grown has been reviewed, discussed, photographed, mocked, praised, prodded, measured, disassembled, and hacked. Until the Internet, little of this social life was available; now there's a flood.
The digitally accessible information about an object can be called its information shadow. [Footnote: The use of "shadow" to describe a relationship between physical objects and digital information goes back to Westin's 1967 description of "data shadows." My use is closest to Greenfield's 2006 use of it: "the significance of technologies like RFID and 2D barcoding is that they offer a low-impact way to 'import' physical objects into the datasphere, to endow them with an informational shadow."] Nearly all industrially created objects have rich information shadows, even if those shadows are invisible to their owners and users.
Wine bottles, for example, have very rich information shadows. Along with the traditional bottle-level data (such as when it was bottled, what grapes were used, who bottled it, etc.) wines have a huge social life generated by thousands of websites, blogs, rating services, and books. Wine enthusiasts probably spend as much time discussing wine as they do drinking it, and they've created a lot of content with easily accessible identifiers, namely the vineyard and vintage. [Footnote: Bruce Sterling describes the kind of social relationship we can have with wine in "Shaping Things," his 2005 book-length essay on ubiquitous computing and design.]
Everyday objects have been separated for a long time from their information shadows, as Peter Pan was from his actual shadow. The complexity of finding, organizing and accessing this information divided the world of objects and the world of information shadows. Even if accessible through a computer, information shadows were unavailable when they could provide the most value: in choosing between different products to buy, or in figuring out how to use a new tool. For example, barcodes aren’t human readable. So for a long time, only those with barcode readers and access to specialized databases could use them. [Footnote: This of course is no longer the case, as barcode reading cameraphone applications have proliferated in recent years, but that's a relatively recent phenomenon relative to the three decade-long history of bar codes in common usage.] Which basically only included retailers and their employees. Even then the kinds of data available to retailers were limited. Standard Universal Product Code (UPC) barcodes identify classes of products, not individual things. Moreover, there is no universal database of barcodes. So a retailer's information about a given object is limited to data it has bought or generated on its own. Typically, like the early Borders Books system, retailers only keep enough information around to price items and order more.
A few industries have systematically generated and employed more extensive information shadows. In particular, the manufacturing and shipping industries have been tracking and identifying individual objects for years. In those industries every mile traveled by every piece of inventory directly affects revenue. So manufacturing and shipping systems provide fine-grained information shadows to identify and locate objects. For example, Wal-Mart and the American military—two organizations that ship a huge variety of things to a dizzying number of locations—have enthusiastically adopted identification technology (Myerson, 2006) to increase efficiency.
For consumers, ubiquitous computing attaches the information shadow to the object, like Wendy does to Peter Pan's shadow. It does this using three key technologies:
- Inexpensive machine-readable item-level identification technologies (see Sidebar) uniquely mark every object.
- Wireless networking makes the information shadow of objects accessible to devices in more places.
- Networked information aggregation services create a standard way of accessing information shadows that are produced simultaneously in many places at once.
Sidebar: Item-level Identification Technologies
There are many technologies for identifying individual items. The most basic identification consists of a unique number or code that is somehow associated with metadata about an object. That's how serial numbers on computers and cars work. More interesting effects appear when devices can read identifying codes without human intervention. Here is a sample of such machine-readable identification technologies.- Barcodes. These are most commonly seen representing the Universal Product Code that's on most retail packaging. They are used to uniquely identify items in corporate inventory systems and in certain niche markets, such as wine storage.

Figure 6-3. QR Code that reads "Ubiquitous Computing User Experience Design" when decoded
2D Barcodes. These come in many styles, from the Datamatrix code found on postal service package labels, to exotic fiducial markers used in motion sensing applications. QR Code markers (Figure 6-3), designed for easy reading using mobile device cameras, are increasingly popular.- RFID. Radio Frequency IDs (Figure 6-4) come in many shapes and sizes—from subway access cards, to paper and metal stickers, to ceramic cylinders that sit in the stomachs of cows. Small radios inside them broadcast a unique identifying number. Because radio waves can transmit through solid materials, RFIDs can embedded inside other objects (shipping palettes, clothing tags and animals). Passive RFIDs, the most common kind, gather energy from radio broadcasts received from RFID readers and reflect that energy back to the readers in the form of a wireless stream of data communicating their unique identifier. They do not need their own source of power to function, but consequently work only within relatively short distances. Active RFIDs use their own power sources to transmit data farther, but are more expensive and often require batteries.

Figure 6-4. An RFID attached to a wine bottle (photo Copyright 2007 by Tod E. Kurt, used by permission)
- Smart cards. SIM cards are small processors packaged inside plastic cards. They transmit a unique identifier when in direct contact with a reader. Because they contain an active processor (typically powered through contact with a reader), they are capable of much more complex interaction. Thus, they can encrypt information, require authentication before transmitting their identifier, poll sensors, etc. Smart "buttons" that resemble coin cell batteries are a similar technology. These buttons also communicate through contact with a reader that also acts as a power source.
- Magnetic stripes are familiar from credit cards and hotel entry cards. They are an established technology, and are easily created or changed, but are neither as compact, convenient or secure as some of the others on this list.
- IPv6. For devices that are actively communicating through a network, IPv6 is an extension to the familiar Internet Protocol standard designed to uniquely identify trillions of devices. It was formally defined in the mid-1990s, and while uncommon in current Internet devices, it will likely become an identification standard for smart devices communicating over a network.
It's important to remember that unique identification and machine-readability are different functions enabled by separate technical choices. The methods listed above frequently combine the two, but readability and identification do not depend on each other. A single identification code can be either machine-readable or machine-unreadable and remain unique. An IPv6 address written on a PostIt and stuck to the side of a machine is still unique, but not easily machine-readable. Similarly, it's possible for multiple RFIDs to transmit the same identification code, just as it's possible for two twenty-dollar bills to have the same serial number.
Tomorrow: Chapter 3, Part 3: Point-at Things



